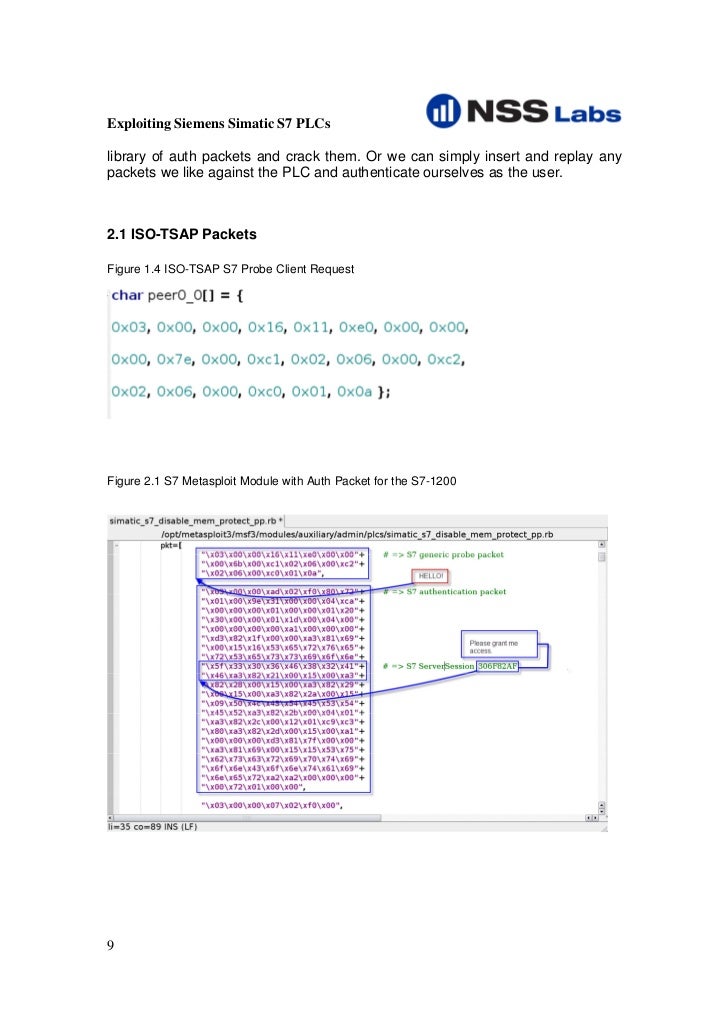
Siemens Step 7 Crack
Siemens Step 7 V14 Crack
OVERVIEW This updated advisory is a follow-up to the original advisory titled ICSA-15-050-01 Siemens SIMATIC STEP 7 TIA Portal Vulnerabilities that was published February 19, 2015, on the NCCIC/ICS-CERT web site. Siemens has identified two vulnerabilities in its SIMATIC STEP 7 (TIA Portal). Siemens has produced a patch that mitigates these vulnerabilities. These vulnerabilities were initially disclosed to Siemens by the Quarkslab team and Dmitry Sklyarov with PT-Security.
Siemens Step 7 Crack
One of the vulnerabilities is remotely exploitable. AFFECTED PRODUCTS --------- Begin Update A Part 1 of 2 -------- Siemens reports that the vulnerabilities affect the following versions of SIMATIC STEP 7 (TIA Portal): SIMATIC STEP 7 (TIA Portal) V13: All versions prior to V13 SP1 Upd1 SIMATIC STEP 7 (TIA Portal) V12: All versions prior to V12 SP1 Upd5 --------- End Update A Part 1 of 2 -------- IMPACT One vulnerability could allow for a successful man-in-the-middle attack, allowing the attacker to view and modify data sent between the user and the system. The other allows a user with local access the ability to reconstruct passwords. Impact to individual organizations depends on many factors that are unique to each organization. NCCIC/ICS-CERT recommends that organizations evaluate the impact of these vulnerabilities based on their operational environment, architecture, and product implementation.